Nvidia Announces Artificial Intelligence Mind for Robots
Introduction Nvidia announces as part of the GTC autumn event that jetson integrating systems are updating with the design on…
QA Fundamentals: Building Quality Into Software Development
QA Fundamentals: Building Quality Into Software Development Quality Assurance (QA) is a method employed in various industries to verify that…
Selenium Mobile Testing: Building Robust Mobile Web Test Suites
Selenium Mobile Testing: Building Robust Mobile Web Test Suites The modern app market is truly and steadily becoming more and…
How Are Microcomputers Made?
Introduction The transistors are used in microcomputers processors and memory and consume less energy than bipolar transistors but are made…
Best Xbox Consoles
Introduction Microsoft’s Xbox platform has various control arms that you can use with it. The quality of these arms and…
The Future of Gaming Technology
The gaming business has made some amazing progress since its beginning, persistently advancing to give players more vivid and practical…
Can Humans Interact With Robots And Teach Them Social Skills?
Introduction Some of the workers conducted a small study published in the journal plus one on human interaction with robots….
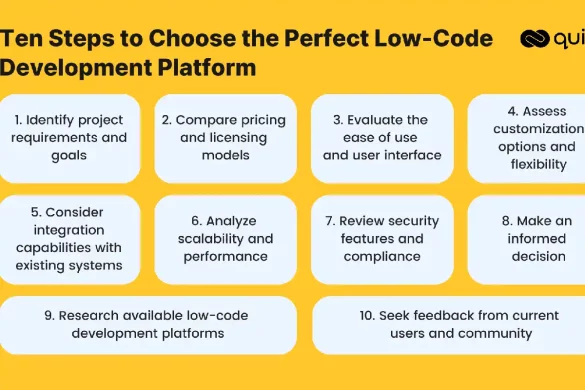
Guidelines For Low-Code App Development Success
Low-code solutions have become more and more popular. It is not a surprise for people from the coding industry as…