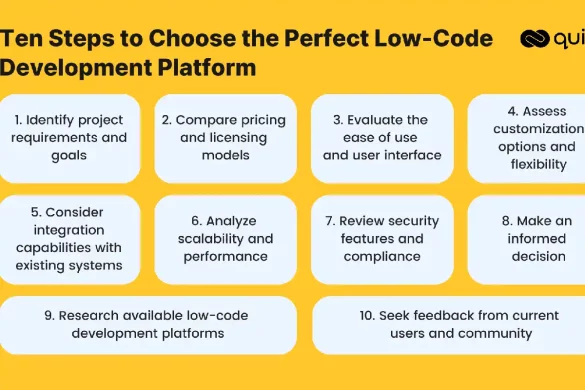
Guidelines For Low-Code App Development Success
Low-code solutions have become more and more popular. It is not a surprise for people from the coding industry as…
What Are Your Options If You Have a Laptop Without WiFi?
A laptop without WiFi does not sound like a good option. For one, many people are too dependent on the…
Maximizing the Value of Managed IT Services: Effective Communication with IT Support
In today’s technology-driven world, businesses rely on managed IT services to keep their operations running smoothly and efficiently. These services,…
What is An Uberduck AI? How It Work, And What are It Features And More
Introduction Uberduck AI – This audio in the voice of AI Or others celebrates the voice. It’s a tool which…
Creative Virtual Event Ideas for Business Companies
Thanks to virtual reality (VR) and augmented reality (AR), among other technologies, it’s now conceivable to organize events, even over…
Post-Quantum Encryption – 2023
Introduction A team from Munich Technical University designed a computer chip that efficiently implements post-quantum encryption. These chips may protect…
untangling the knot: enabling rapid software evolution
Introduction Untangling the knot: enabling rapid software evolution this topic narrated by james Ivers on September 10 2020. Meanwhile, in…
5 Qualities to check to align with the best virtual desktop provider
A virtual desktop is a software application that enables users to run multiple programs on a computer screen. Because they…